 VulnZap
VulnZapThe authorization layer
for browser execution
Control what your AI agents can and cannot do with enforceable tool and data policies. Deterministic guardrails for autonomous AI agents.
The deployment gap
65% are experimenting. Only 11% are shipping.
The blocker isn't capability. It's authorization.
Gartner, 2025
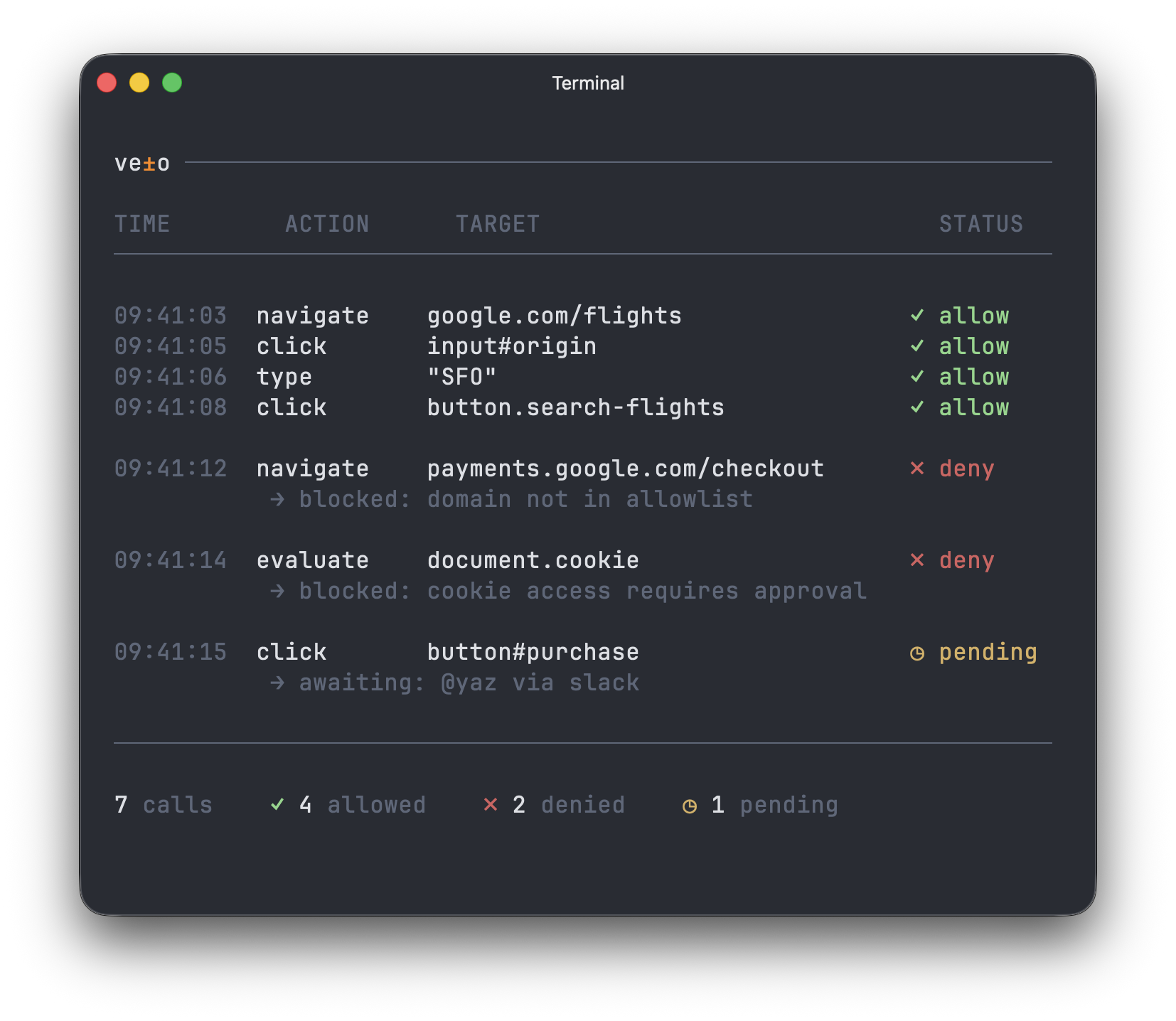
What happens when your agent goes rogue?
This is what "autonomous" looks like without authorization.
Every generation builds a permission layer.
Before: programs destroyed each other.
After: multi-user computing.
Before: passwords flew in plaintext.
After: e-commerce.
Before: apps had full device access.
After: the app economy.
Authorization primitives
Policy enforcement
Allow, deny, or require approval. Per domain, per action, per selector.
Real-time interception
Every tool call passes through Veto before execution. <5ms overhead.
Human-in-the-loop
Route sensitive actions to Slack, email, or dashboard for approval.
Full audit trail
Every decision logged. Searchable, exportable, compliance-ready.
Declarative policy example
Drop in. Lock down.
Three lines of code. Full authorization control.
import { chromium } from 'playwright'import { Veto } from 'veto'const browser = await chromium.launch()const page = await browser.newPage()const tools = [ { type: 'function', function: { name: 'browser_navigate', description: 'Navigate to a URL', parameters: { type: 'object', properties: { url: { type: 'string' } }, required: ['url'] } } }, { type: 'function', function: { name: 'browser_click', description: 'Click a selector', parameters: { type: 'object', properties: { selector: { type: 'string' } }, required: ['selector'] } } }]const toolHandlers = { browser_navigate: async ({ url }: { url: string }) => page.goto(url), browser_click: async ({ selector }: { selector: string }) => page.click(selector)}const veto = await Veto.init()const wrappedTools = veto.wrap(tools)await agent.run('Book a flight under $400', { tools: wrappedTools, toolHandlers })Works with your stack
Drop-in integration with popular agent frameworks
Pricing
Start free. Scale when ready.
Free
- 10K decisions/mo
- 1 agent
- 7-day logs
- Local policies
Team
- 100K decisions/mo
- 10 agents
- 30-day logs
- Cloud dashboard
Business
- 1M decisions/mo
- Unlimited agents
- 90-day logs
- Managed policies
Enterprise
- Unlimited decisions
- Unlimited agents
- Custom retention
- Custom policies
Sign up now and we'll notify you when your account is ready.
Sign up with WorkOSHave a pilot invite code? Enter it here
FAQ
Veto wraps your browser automation library and intercepts every action before execution. Each action is evaluated against your policy rules, which can allow, deny, or require human approval.